
Egregious examples such as the LandWind X7 hit the news headlines, but with the industry operating across tiers on a globally dispersed basis, much engineering data is moved, transferred, shared – and all too often misappropriated and passed off. Aside from commercial theft, rogue states seeking to fast-track their domestic automotive industries now have to be added to the list of threat agents. Digital transformation and security experts Majenta Solutions has launched a new form of data transfer technology to help address industry concerns.

Can you tell us a little about Majenta Solutions?

Discover B2B Marketing That Performs
Combine business intelligence and editorial excellence to reach engaged professionals across 36 leading media platforms.
Majenta has a long history of supporting large OEMs, including Ford and JLR, through to tier suppliers from Astheimer to Prodrive. At the core of our offering is software that allows standards across the supply chain to cohere – whether that be translating engineering drawings from one CAD format to another, to establishing engineering design process integration across multiple parties in the supply chain.
We’re at the coal face, developing systems that exchange engineering drawings, such as our tool, MX. It is not dissimilar in function to WeTransfer, albeit configured for sharing automotive engineering design files. It offers secure transfer and manages an audit trail of sends, receipts and opens so the beneficial IP owner can always see who has accessed the data. MX has been in service for some while and has been the foundation for our next-generation tool, MX ASR, which launched in March 2022.
Please outline the context and current cybersecurity risk for automotive companies and the supply chain.
Current security protocols are being progressively eroded while the operational need to share data is growing exponentially. All this is presenting rich pickings to threat agents.
Cybersecurity has become a significant issue. Just last week, Toyota shut down 14 production lines in Japan due to a data breach. The threats rarely manifest when data is at rest, but when it is being moved from one place to another. Data has therefore become the new ‘oil’ and the automotive industry’s protections lag behind the will and capability of so-called threat agents who seek to profit from the misappropriation of vital IP.
The other challenge on the horizon is the advent of quantum computing; the computational power inherent in quantum machines will render useless traditional encryption capabilities normally used to protect the process of relaying data from point to point. MX ASR is where the fight back begins using a completely new and revolutionary technology. Our new MX technology, MX ASR, is quantum-secure by virtue of its patented ‘sharding’ treatment of data.
How does ‘sharding’ work and why is it superior to encryption?
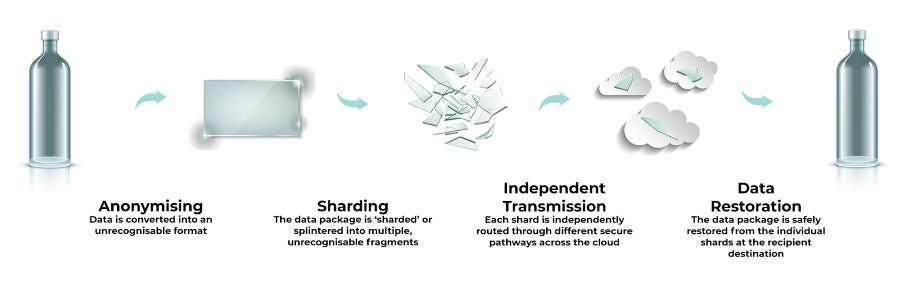
Rather than encrypt a file, send it and de-encrypt it, sharding breaks down the file into smaller components – think of a glass bottle being the file and when it is smashed, the fragments are the shards. The shards are then transmitted independently across the cloud, using different routing paths before they re-assemble at the recipient end point, making each shard anonymous. If a shard is intercepted along the way, it has no data integrity and cannot be opened independently of the other shards. The solution avoids the problems of encryption that sends a file as one transmission, which can be intercepted and, in time, the encryption methodology will fall victim to quantum resolution.
How has it been tested against possible threat agents?
The technology is mathematically impenetrable. Validation was assessed by the UK Ministry of Defence through extensive research. It identified that brute force attacks against anonymised and sharded data would be unsuccessful and that the ASR process would be immune to quantum computing-based brute force attacks. The ASR process provides perfect secrecy against a threat actor having access to anything less than the total number of shards.
What’s the scale of the problem?
A 2021 survey of the 14 OEMs responsible for $1.1 trillion in car industry revenue annually by CyberAware identified over 800,000 unprotected documents hosted on exposed servers, clouds, and databases, with 215,000 employees having exposed or compromised credentials. Just one sample manufacturer in the analysis had an AWS S3 bucket exposing five million files. The exposed information included commercial details, email exchanges, contracts, invoices, and technical data.
While the industry is under-prepared, the threat landscape is growing exponentially. The UK government’s Cyber Security Breaches Survey 2021 reports that six in ten medium-sized and larger companies (in all industries) suffered attacks in 2021 and a quarter of businesses report an astonishing weekly frequency of breaches; 40% of these occurrences result in a material loss to the companies involved.
How do customers access this technology?
MX ASR is a subscription-based SaaS desktop tool – it is simple to download and install, and easy to use. There is no need for complex deployment by IT technicians across global operations, and there is no limit to the size of files that can be transferred.
Who are you providing this solution to in the automotive sector? Can you provide examples of use cases?
A typical use case might be an OEM in Japan consulting with a tier supplier designing a gearbox in the US, with a number of tier two suppliers in the UK and Germany specifying gearbox housings and internals. In this simplified example, the CAD files for the design need to be shared across six or seven organisations on three continents. The sub-assembly has cost $2.5m to design and develop, as well as sitting on the critical time path of the vehicle development. Protecting this exchange of data is imperative.
What is your outlook for data security in the automotive industry, and what role could MX ASR play? Does it have wider applications within automotive data?
Yes, any engineering-based industry that operates a tiered supply chain that is dispersed in many geographical locations also faces the same challenges. MX is in use by many aerospace companies for instance, where the IP is valuable and the sharing requirement is complex.
We believe that MX ASR will change the landscape of commercial and industrial data integrity in favour of business. It delivers a new generation of impenetrable security, a host of features that have evolved from MX’s lengthy experience of supporting the requirements of business workflows and above all, it is quick and easy to adopt.






